- Home
- >
- Cloud & AI
- >
- Flow Logs
- >
Flow Logs
2025-12-11 16:24Flow Logs (FL) provide a full-time, full-flow, and non-intrusive traffic collection service for you. You can perform real-time storage and analysis of network traffic, helping you address issues such as troubleshooting, architecture optimization, security detection, and compliance auditing, making your cloud network more stable, secure, and intelligent. As a mature core network monitoring product, Flow Logs (FL) employ non-intrusive side-path collection technology, avoiding the consumption of cloud host resources. Flow Log Collection covers the traffic of all Elastic Network Interfaces across the entire network, recording key fields such as source IP, destination IP, and protocol, achieving full-time, full-flow data retention. Flow Log Query supports second-level retrieval of billions of data entries, enabling quick pinpointing of key information through multi-keyword filtering. Network Architecture Optimization leverages traffic data analysis to help build baseline models, troubleshoot performance bottlenecks, and expand business coverage domains. Network Threat Alert can identify abnormal communication behavior, enabling security risk warnings without affecting host performance. Whether for rapid troubleshooting of network faults, detailed optimization of architecture, or proactive prevention of potential threats, Flow Logs (FL) can become the core support for stable operation of enterprise cloud networks through the comprehensiveness of Flow Log Collection, the efficiency of Flow Log Query, the practicality of Network Architecture Optimization, and the foresight of Network Threat Alert. Furthermore, the deep synergy between Flow Log Collection and Flow Log Query significantly enhances the operational efficiency and security value of Flow Logs (FL).
Frequently Asked Questions
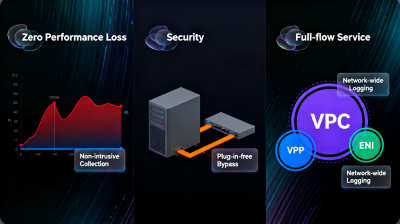
Q: As the core data foundation, how does Flow Log Collection synergize with Flow Log Query and Network Threat Alert to support the core needs of Flow Logs (FL) and Network Architecture Optimization? Where are its technical advantages reflected?
A: Centered on "Full Collection + Non-intrusive," Flow Log Collection provides data support for two core capabilities, solidifying the service foundation of Flow Logs (FL). Firstly, through full-time, full-flow collection of Elastic Network Interface traffic, it completely records key traffic fields, providing massive and accurate raw data for Flow Log Query. Simultaneously, it coordinates with Network Threat Alert to monitor abnormal traffic characteristics in real-time (e.g., communication with threat IPs, access via uncommon protocols), enabling rapid identification of security risks. Secondly, it provides data basis for Network Architecture Optimization. Historical traffic data collected through Flow Log Collection can be used to establish business network baselines. Through multi-dimensional analysis via Flow Log Query, it helps locate issues such as excessive bandwidth usage or performance bottlenecks, assisting in architecture adjustment and resource optimization. Technical advantages are evident in two aspects: First, "Zero Overhead + Complete Coverage" – non-intrusive collection avoids consuming cloud host CPU and bandwidth, and full-flow collection ensures no critical traffic data is missed, making the monitoring of Flow Logs (FL) more reliable. Second, "High Real-time Capability + Easy Coordination" – real-time collection meets the immediate warning needs of Network Threat Alert, and its structured data format is compatible with the efficient retrieval of Flow Log Query, providing precise data support for Network Architecture Optimization.

Q: What is the core synergistic value between Network Architecture Optimization and Network Threat Alert? How can Flow Log Collection and Flow Log Query be leveraged to strengthen the competitiveness of Flow Logs (FL)?
A: Their core synergistic value lies in the two-way empowerment of "Proactive Optimization + Risk Prevention," addressing the pain point in network operations where "only faults are resolved, risks are not prevented." Network Architecture Optimization focuses on enhancing network efficiency by optimizing resource allocation through traffic analysis. Network Threat Alert focuses on preemptively preventing risks by identifying abnormal behavior to avoid security incidents. Their combination elevates Flow Logs (FL) from a "passive operational tool" to an integrated solution for "Proactive Optimization + Risk Prevention." Their synergy with Flow Log Collection and Flow Log Query significantly enhances the competitiveness of Flow Logs (FL): Flow Log Collection provides comprehensive data support for both, recording normal traffic data for Network Architecture Optimization analysis while capturing abnormal traffic characteristics for Network Threat Alert identification. Flow Log Query enables rapid filtering and in-depth mining of data, helping extract key metrics for architecture optimization from massive collected data, while precisely locating the specific source and communication path of network threats. This combination of "Efficiency Enhancement + Risk Prevention + Full Collection + Efficient Query" gives Flow Logs (FL) stronger market competitiveness.
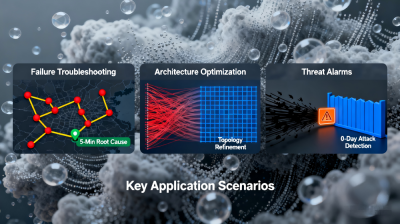
Q: How does Flow Log Query address the data processing pain points in network operations? What benefits does its synergy with Flow Logs (FL) and Flow Log Collection bring to Network Architecture Optimization and Network Threat Alert?
A: The core value of Flow Log Query lies in "Billions of Data + Second-level Response," solving the traditional network log pain points of "slow queries, difficult filtering, and low efficiency." Through features like multi-keyword search and precise field filtering, it transforms massive flow log data into valuable operational information. Its synergy with the two core components brings significant gains to scenario-specific capabilities: Working with Flow Logs (FL) and Flow Log Collection, Flow Log Query enables in-depth analysis of all collected data, providing precise evidence for Network Architecture Optimization. For example, it can optimize subnet division by analyzing traffic distribution or expand node deployment based on access regions. For Network Threat Alert, Flow Log Query can quickly correlate contextual information about abnormal traffic, such as identifying the communication frequency of a threat IP or the business ports involved, helping to rapidly assess risk levels and formulate response strategies. Simultaneously, the second-level response capability of Flow Log Query significantly improves the handling efficiency of Network Threat Alert. This synergy makes the decision-making for Network Architecture Optimization more scientific, the response to Network Threat Alert faster, and the data analysis capability of Flow Logs (FL) better aligned with enterprise operational needs.